Detect vulnerabilities. Your attack surface incorporates your whole access details, such as Every single terminal. But In addition it contains paths for information that shift into and out of applications, along with the code that shields People significant paths. Passwords, encoding, plus much more are all provided.
As soon as you’ve obtained your men and women and procedures in position, it’s time to figure out which technological innovation tools you want to use to shield your Personal computer methods towards threats. From the era of cloud-indigenous infrastructure where remote function is now the norm, safeguarding against threats is a complete new problem.
Companies may have information security professionals carry out attack surface Examination and management. Some Concepts for attack surface reduction incorporate the subsequent:
Tightly built-in item suite that allows security teams of any sizing to promptly detect, investigate and respond to threats through the organization.
Underneath this design, cybersecurity pros call for verification from every supply no matter their position inside of or outdoors the community perimeter. This necessitates implementing rigorous obtain controls and procedures to aid Restrict SBO vulnerabilities.
One notable occasion of the electronic attack surface breach transpired when hackers exploited a zero-day vulnerability in the extensively used software.
Specialised security platforms like Entro will help you obtain real-time visibility into these typically-neglected components of the attack surface so as to improved determine vulnerabilities, implement least-privilege access, and put into practice efficient secrets rotation insurance policies.
For example, intricate systems may result in customers accessing assets they do not use, which widens the attack surface accessible to a hacker.
Why Okta Why Okta Okta offers you a neutral, powerful and extensible System that places identity at the heart within your stack. It doesn't matter what industry, use circumstance, or volume of support you require, we’ve bought you coated.
With much more possible entry factors, the probability of A prosperous attack increases greatly. The sheer quantity of systems and interfaces helps make checking difficult, stretching security teams skinny as they try to secure a vast assortment of likely vulnerabilities.
Empower collaboration: RiskIQ Illuminate permits enterprise security teams to seamlessly collaborate on risk investigations or incident reaction engagements by overlaying inside knowledge and menace intelligence on analyst success.
Embracing attack surface reduction strategies is akin to fortifying a fortress, which aims to attenuate vulnerabilities and Restrict the avenues attackers can penetrate.
This process thoroughly examines all details where an unauthorized consumer could enter or extract facts from the technique.
Zero belief is a cybersecurity system the place every single consumer is confirmed and each connection is licensed. No-one is provided use of means by default.
 Spencer Elden Then & Now!
Spencer Elden Then & Now!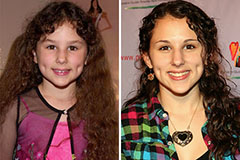 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Alexa Vega Then & Now!
Alexa Vega Then & Now! Dolly Parton Then & Now!
Dolly Parton Then & Now! Megyn Kelly Then & Now!
Megyn Kelly Then & Now!